Table of Contents
PC running slow?
In the past few days, some readers have come across an error code with the win32 delf bs proxy trojan. This problem occurs for several reasons. Let’s look at them now.
(Proxy .LRT, system error, TROJ_DELF.IJA, Proxy.MFL, Cryp_Yodap, parser error, TrojanProxy: Win32 / Delf.W, TrojanProxy: Win32 / Delf, Win32 / Delf, Generic.dx, PWS-Banker, Trojan- Proxy.Win32.Delf.bs, TR / ATRAPS.Gen, TROJ_DELF.DWG, TR / Proxy.Delf.BS.371, Proxy.SHN, PWS-Banker.gen.ce, Trojan.Proxy.Delf. BS, TR / Spy.Banker.Gen, TR / Proxy.Delf.BS.310, Trojan-Spy.Win32.Banker.cho, TR / Dldr.Delphi.Gen)
Added virus description: April 26, 2007
(Trojan-Proxy.Win32.Delf.bs, W32 / Trojan.ABIH, TR / ATRAPS.Gen, TR / Proxy.Delf.BS.195, Proxy.LAK, Cryp_Yodap, parser error, TR / Proxy. Delf .BS.204, TrojanProxy: Win32 / Delf.W, PWS-Banker.gen.ce, Generic.dx, Trojan.Proxy.Delf.BS, Backdoor: Win32 / Agent, Trojan.Downloader.Delf.AGJ, TR / Spy .Banker.Gen, Trojan-Spy.Win32.Banker.cho, PSW.Banker3.IFH, Win32 / Agent)
Virus summary added: 12 April 2007
A destructive hacker can use this threat to reveal his identity when performing actions caused by your computer. This may include sending direct mail through your Internet connection.
Find out how malware can get onto your computer.
What To Do Now

Use old Microsoft free software to detect and fixfor this threat:
- Windows Defender for Windows 10 and 8 windows.1 or Microsoft Security Essentials for Windows 7 and Windows Vista
- Microsoft Security Scanner
A full scan is also recommended. When fully launched, other hidden malware may be detected.
Get More Help
You can also visit our advanced page or visit the Microsoft Virus and Malware website for more help
If you’re using Windows XP, see our Windows XP Security page.
This Trojan horse enters the absolute system as a file dropped by various other malicious programs, or as a file downloaded without the knowledge of users when visiting malicious websites.
However, even at the time of writing, these pages should not be available.
Arrival information
This Trojan enters the system as a real file dropped by other malware, or as the fact that “the file is being downloaded unknowingly users whovisit malicious sites a second time.
Installation
This Trojan will keep the following copies even on the system:
- % System Root% RECYCLER SID nvapbar.exe
(Note:% System Root% is the Windows root folder, which can usually be called C: in all Windows operating systems with different versions of the system.)
The following will follow the created folder :
- % System Root% RECYCLER
- % System Root% RECYCLER SID
(Note:% System Root% is the root folder of Windows, usually C: in all versions of the Windows operating system.)
Autorun Technique
This Trojan creates the following registry entries. to automatically execute remote components on almost every system boot:
HKEY_LOCAL_MACHINE SOFTWARE Microsoft
Windows NT CurrentVersion Winlogon
Taskman =% System Root% RECYCLER SID nvapbar.exe
More info
This Trojan horse connects to a potentially malicious URL:
- ChatAddiction .BLOCKEDsers.com
- BF2GameServices.BLOCKEDme. org
- utgameserver325 .BLOCKEDs.be
However, the specified websites are not available.
Step 1
Windows XP, Windows Vista, and Windows 7 users must restore their systems before deploying a scan.To him. Disable creation to allow full scans. your computers.
Step 2
Please note that while this malware spies on files, all ring folders as well as registry keys and entries attached to your computer configured as software / unwanted software. This could be due to incomplete installation or other system conditions. If you cannot find the files / folders / registration information you want, go to the second step.
Step 3
Restart in Safe Mode
[Learn more]
Step 4
PC running slow?
ASR Pro is the ultimate solution for your PC repair needs! Not only does it swiftly and safely diagnose and repair various Windows issues, but it also increases system performance, optimizes memory, improves security and fine tunes your PC for maximum reliability. So why wait? Get started today!

Delete this single registry value
[Learn more]
Important: Incorrectly editing this specific Windows registry may cause irreparable system operation. Please follow this step if you know how to ask a question, or if you are very good at asking your system administrator for help. Otherwise read this Mic articlerosoft before setting up your computer’s registry.
- In HKEY_LOCAL_MACHINE SOFTWARE Microsoft Windows NT CurrentVersion Winlogon
- = Taskman root% RECYCLER SID nvapbar “% system.exe”
Step 5
Find and delete these folders
[More]
Make sure you check the “Search for hidden files and folders” checkbox in the “Additional advanced options” section, which can include all hidden folders in the scan result.
- % System Root% RECYCLER SID
Step 6
Reboot normally and scan the computer on which the Trend Micro product is installed for files detected as Trojan.Win32.DELF.BA If the detected files have already been cleaned, deleted, or quarantined, they belong to the Trend Micro product, no other path is required. you can partially remove files from quarantine. More information can be found here on the knowledge page.
Was this unique description helpful to you? Tell us how we both got along.
This Trojan horse enters the system and sees a file dropped in it other malware, or possibly a file unknowingly downloaded by addicts who visit malicious websites.
This Trojan is detected in the system as a file that is absent on other computers, or as malware in the form of a database that users unknowingly download when they visit malicious websites.
This Trojan places the following copies of itself on the affected system:
- % System Root% RECYCLER SID nvapbar.% System exe
(Note: Root% is the main Windows folder, which is usually C: for all versions of the Windows operating system.)
- % system backbone% RECYCLER
- % system backbone% RECYCLER SID
(Note:% System Root% is the Windows root file, usually C: on all versions of the Windows operating system.)
This Trojan horse forces the following registry entries to allow saved components to run automatically on every system boot:
This Trojan connects to one of the following potentially malicious URLs:
- ChatAddiction.BLOCKEDsers.com
- BF2GameServices.BLOCKEDme.org
- utgameserver325.BLOCKEDs.be
Before scanningm Windows XP, Windows Vista and Windows 7 users must uninstall System Restore so that their computers can be fully scanned.
Please note that not all files, files, registry keys and entries are created on your computer while malware / spyware / grayware uses this feature. This may be due to incomplete installation or other system conditions. If you cannot find the same files / folders / registration information, go to a new step.
Important: Incorrectly editing the Windows registry can cause irreversible system malfunction. Please only do this step if the public knows how to request control from your sysadmin. If not, read this Microsoft article now before editing your personal registry.
- In HKEY_LOCAL_MACHINE SOFTWARE Microsoft Windows NT CurrentVersion Winlogon
- Taskman “% System matches root% RECYCLER SID nvapbar.exe”
< / ul>
Be sure to check the Scan for hidden files and folders box in the Advanced Settings”to include all hidden folders in the scan result.
- % System Root% RECYCLER SID
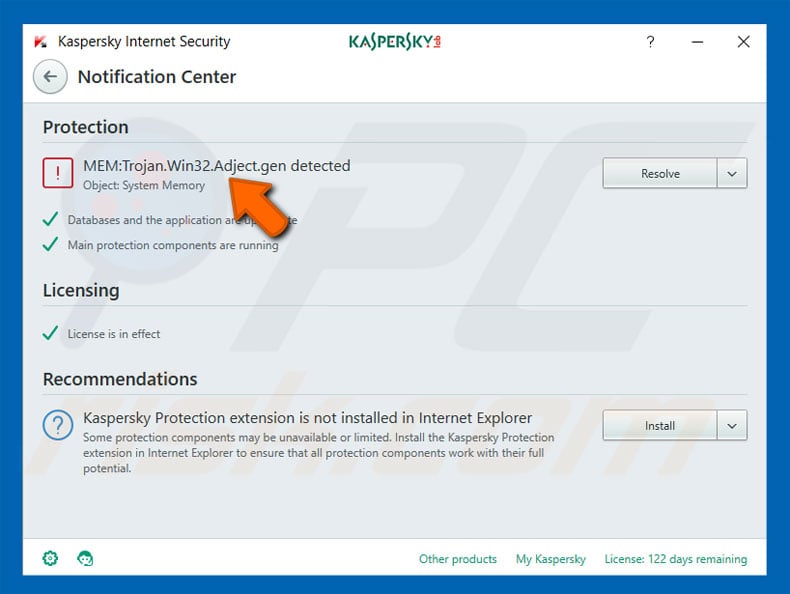
Restart in known mode and use your computer to scan your Trend Micro product for files found on Trojan.Win32.DELF.BA. If the detected files have been cleaned, deleted, or quarantined with a Trend Micro product, no further action is required. You can simply remove duplicate content from quarantined files. Please refer to this knowledge base for more information.
Improve the speed of your computer today by downloading this software - it will fix your PC problems.
Stappen Om Win32 Delf Os Proxy Trojan-problemen Op Te Lossen
Passaggi Per Risolvere I Problemi Del Proxy Trojan Del Computer Win32 Delf
Étapes Pour Résoudre Les Problèmes De Cheval De Troie Proxy Win32 Delf Os
Etapas Quando Você Precisa Corrigir Problemas De Cavalo De Tróia Win32 Delf Os Proxy
트로이 목마 문제가 발생하도록 Win32 Delf Os 프록시를 적극적으로 수정하는 단계
Steg För Att åtgärda Win32 Delf Os Proxy Trojanproblem
Schritte Zur Behebung Von Win32-delf-OS-Proxy-Computervirenproblemen
Действия по устранению проблем с троянскими программами Win32 Delf OS
Kroki, Aby Rozwiązać Problemy Z Trojanem Win32 Delf Os Proxy
Pasos Para Solucionar Problemas De Malware De Proxy Win32 Delf Os