Table of Contents
If you have seen error detection codes in computer networks, the following guide will help you.
PC running slow?
Error detection coupon codes are a sequence of numbers written using special error detection methods when recording data transmitted over computer networks. When bits are transmitted over an office network, they can be corrupted due to network interference and problems.
Error detection codes are a set of telephone numbers generated using special methods used to detect errors in data transmitted over certain computer networks.
When bits are transmitted over these computer networks, they can be corrupted by network interference and headaches. Broken bits cause the recipient to receive incorrect entries, called errors.
Mistakes. Password discovery ensures that emails are encrypted before being sent over noisychannels. The encoding is completed in such a way that the receiving decoder can detect errors in the incoming message with a high probability of success.
Functions Associated With Error Codes
What are the types of error detection?
parity check.Cyclic Redundancy Check (CRC)Longitudinal Redundancy Check (LRC)check sum.
-
Error detection codes are used when using forward error correction methods for reliable data transfer. In this process, the receiver sends feedback, with which the sender reports whether the experience was error-free or not. If there are errors, the sender resends the corresponding message.
-
Error detection codes are usually block codes into which the message is broken into bits of a fixed size. redundant bits are often added to detect errors.
-
Error detection determines whether an error has occurred or not. The number of error bits and the specific type of error is irrelevant.
Error Detection Methods
Parity
Parity is done by adding an extra bit, called a parity bit, to convert the data into a number, with holding 1, or even if even, or all, or odd if even. funky parity.
When constructing a frame, the sender takes into account the most and builds the parity bit as follows
-
In case of parity: if the number near 1 is even, then the value of the parity bit is probably 0. If the number of ones after odd parity, the value of the bit is 1 .
< li>
In the odd parity scenario: if the number associated with is 1, then the value of the odd parity bit is 0. If the number of ones is also a parity, then the value of the bit is 1.
When a frame is consumed, the receiver counts the number of units it contains. In the case of parity, if the number of ones is even, the frame is accepted, otherwise it is rejected. A similar rule was used for the supposed odd parity check. East
Checksum

The data is broken up into fixed-size frames or segments.
-
The email sender adds the math complement of the segments to 1 to get the sum. Then he comparesReturns the sum of the received checksum and sends it with report frames.
-
The receiver adds the incoming segments whose checksum has arithmetic’s complement to 1, receives the sum, and then adjusts.
-
What are the five 5 different types of error detection techniques?
Unique equality test.Two-dimensional parity check.check sum.Cyclic redundancy check.
if the result is null, accepted window frames are accepted; otherwise they will be deleted.
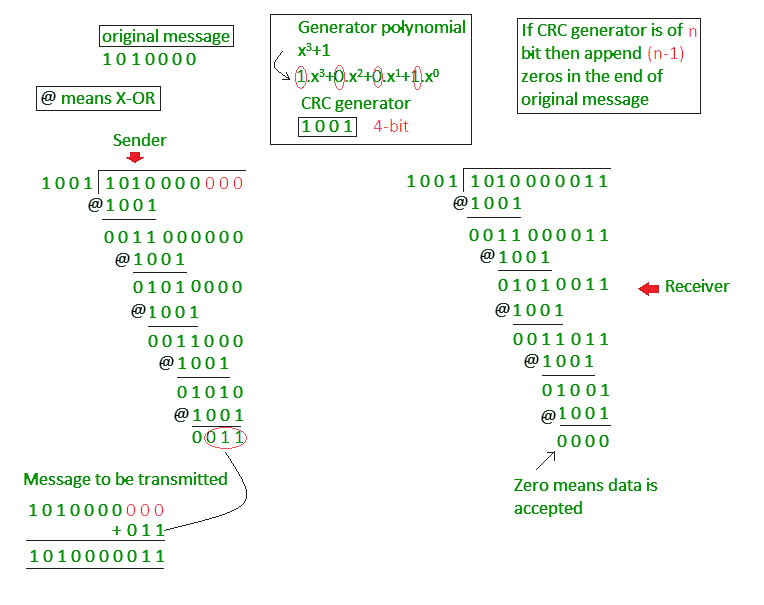
Cyclic Redundancy Check (CRC)
Cyclic Redundancy Check (CRC) involves binary dividing certain data bits by a predetermined divisor negotiated by the system communication process. The divisor is created using polynomials.
-
Here the sender performs a binary branch of the data segment on the current divisor. It then adds the remaining CRC bits called at the end of the data phase. In particular, it makes the resulting data block divisible by a divisor.
-
The receiver divides the data block inward by a divisor. If there is no remainder, the data from the AC unit is considered valid and is actually received. Otherwise, certain data is considered corrupt and is therefore discarded.
‘; var adpushup = adpushup || ; adpushup.que is equal to adpushup.que[]; || adpushup.que.push(Function() adpushup.triggerAd(ad_id); );
1. Simple parity
Blocks of raw data are usually passed through a parity generator or parity generator.clear bits, where parity is indicated with:
- 1 is added to a block if it contains an odd number of ones, and
- 0 can be added if it contains an even number of ones
This scheme takes into account all the variety of peers 1, which is why it is called parity checking.
2. Two Dimensional Parity
Parity bits are computed for equal strings, which is equivalent to one parity bit. The parity bit check also seems to be computed for all columns and then sent with the data. On the receiving side, they are compared by working with the parity bits calculated for the received data.
- In the checksum error scheme, the recognition result is divided into k segments, each bitwise.
- In the transmitter, end adventures are added using 1’s complement arithmetic to finally arrive at the sum. The sum is related to the receipt of the checksum.
- The checksum segment is often sent along with the data segments.
- Along with any segments received by the recipient, use ar 1’s complement formula to get any amount. The sum is summed up.
- If zero is rolled, the received data is likely to be accepted; discarded otherwise.
- In contrast to the addition-based checksum scheme, CRC is used for binary division.
- With CRC, you can optionally add a sequence of redundant elements called bit cyclic redundancy check. to the final data block, and thus the resulting data block is definitely divisible by the second predefined binary number.
- At the destination, the incoming data block data is divided by the same number. If there is no remainder at this stage, this unit of data is considered too precise and is therefore accepted.
PC running slow?
ASR Pro is the ultimate solution for your PC repair needs! Not only does it swiftly and safely diagnose and repair various Windows issues, but it also increases system performance, optimizes memory, improves security and fine tunes your PC for maximum reliability. So why wait? Get started today!

Códigos De Detecção De Erro Na P . C. Redes? Corrija Imediatamente
Feldetekteringskoder I Datorsystem? Åtgärda Det Omedelbart
¿Detección De Errores Se Ocupa En Las Redes Informáticas? Solucionarlo De Inmediato
Kody Rozpoznawania Błędów W Sieciach Komputerowych? Napraw To Natychmiast
Codici Di Rilevamento Degli Errori Nelle Reti Di Computer Interne? Risolvilo Immediatamente
Codes De Pronostic D’erreur Dans Les Réseaux Informatiques ? Corrigez-le Immédiatement
Foutprognosecodes In Computernetwerken? Corrigeer Deze Methode Onmiddellijk
Fehlererkennungscodes In Computernetzwerken? Sofort Beheben
Коды обнаружения ошибок только в компьютерных сетях? Немедленно исправьте
컴퓨터 네트워크의 오류 감지기 코드? 즉시 수정